Reminder to use strong passwords
-
Just got done investigating a spambot we had earlier, and it looks like they used a lot of compromised accounts on other instances to give their post an initial upvote boost. If you don’t already, please remember to use a good strong password. Keeping your account secure helps reduce spam across the whole of lemmy, and keeps your account from getting banned for things you didn’t actually do.
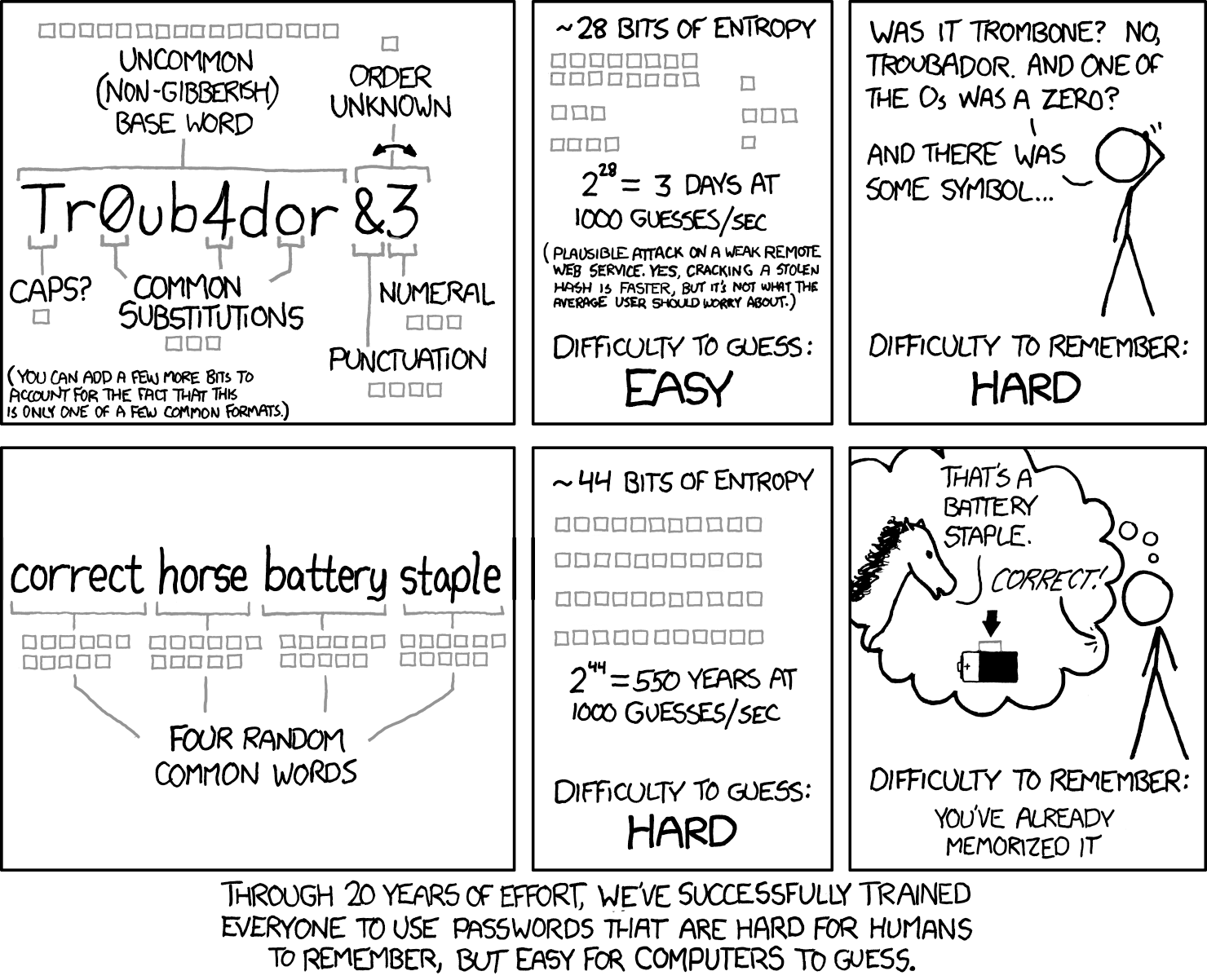
I recommend Diceware! I use it in my professional capacity as an IT/Security person, and also you get to use your mathrocks!
EDIT: Oh, also, all that numbers and symbols shit is no longer considered good practice. Just make it a really long collection of random words, at least 12, ideally 16+ characters. And make sure the words are actually random; your 3 favorite sports teams isn’t good enough, which is why I recommend diceware.
Random passwords are good practice, what isn’t good practice is following specific password requirements like 10 characters 1 uppercase, 1 symbol because that reduces your search space. A 30 or 50 character password generated by your password manager is always the most secure option, the longer the better. I generate passwords that go to the maximum the service allows.
-
Just make one super strong password, use that to unlock you password manager and have it generate 30 character passwords for everything.
Ideally all lowercase letters to make them easy to type when you need to use them in another device. Unfortunately, a lot of places don’t allow that, preferring less secure and more inconvenient passwords.
-
Random passwords are good practice, what isn’t good practice is following specific password requirements like 10 characters 1 uppercase, 1 symbol because that reduces your search space. A 30 or 50 character password generated by your password manager is always the most secure option, the longer the better. I generate passwords that go to the maximum the service allows.
“Password must be between 8 and 12 characters”


 ️
️ -
Just got done investigating a spambot we had earlier, and it looks like they used a lot of compromised accounts on other instances to give their post an initial upvote boost. If you don’t already, please remember to use a good strong password. Keeping your account secure helps reduce spam across the whole of lemmy, and keeps your account from getting banned for things you didn’t actually do.
I recommend Diceware! I use it in my professional capacity as an IT/Security person, and also you get to use your mathrocks!
EDIT: Oh, also, all that numbers and symbols shit is no longer considered good practice. Just make it a really long collection of random words, at least 12, ideally 16+ characters. And make sure the words are actually random; your 3 favorite sports teams isn’t good enough, which is why I recommend diceware.
Also: Reminder to enable 2 factor authentication, of you haven’t.
-
This is what you get for making me admin, I’ve gone mad with power, muhahahahaha!
crimes o-o
-
Just make one super strong password, use that to unlock you password manager and have it generate 30 character passwords for everything.
Password managers are OK but I have hesitations on them personally. I’m leery of putting all my most high-value stuff in one place behind one password. What I do instead is memorize a truly unreasonable amount of passwords, though, which I recognize is not a reasonable expectation for others. For threat models in which you’re not worried about in-person attacks, it may actually be a good idea to just write your passwords down, maybe keep your password book in something with a lock on it. I’m not advocating for any particular method, just putting it out there so people can make an informed decision.
-
Diceware is a password locker?
Diceware is a method of generating random memorable passwords.
-
Basically what diceware does. It’s just that humans are really bad at picking random words (“banana” is over represented, for instance) that’s what diceware helps with.
-
Diceware is a method of generating random memorable passwords.
I would suggest a password locker rather than just a generated passphrase.
-
“Password must be between 8 and 12 characters”


 ️
️'Pass word1!
Oh, ’ and spaces aren’t allowed?
-
Basically what diceware does. It’s just that humans are really bad at picking random words (“banana” is over represented, for instance) that’s what diceware helps with.
I used to use words from different vernaculars or languages. Sometimes i double check they are too abstract and weird to correct horse battery staple easily just because I’m a contrarian asshole snd thst helps me remember. exquisitevibrattoacquittalbevelschaudenfreude
-
Just got done investigating a spambot we had earlier, and it looks like they used a lot of compromised accounts on other instances to give their post an initial upvote boost. If you don’t already, please remember to use a good strong password. Keeping your account secure helps reduce spam across the whole of lemmy, and keeps your account from getting banned for things you didn’t actually do.
I recommend Diceware! I use it in my professional capacity as an IT/Security person, and also you get to use your mathrocks!
EDIT: Oh, also, all that numbers and symbols shit is no longer considered good practice. Just make it a really long collection of random words, at least 12, ideally 16+ characters. And make sure the words are actually random; your 3 favorite sports teams isn’t good enough, which is why I recommend diceware.
Horse: “That’s a battery staple.”
Man: “Correct!”
-
these are called pass phrases and yes, they tend to be way more secure at least until quantum computers render all traditional cryptography meaningless.
-
Password managers are OK but I have hesitations on them personally. I’m leery of putting all my most high-value stuff in one place behind one password. What I do instead is memorize a truly unreasonable amount of passwords, though, which I recognize is not a reasonable expectation for others. For threat models in which you’re not worried about in-person attacks, it may actually be a good idea to just write your passwords down, maybe keep your password book in something with a lock on it. I’m not advocating for any particular method, just putting it out there so people can make an informed decision.
I’m leery of putting all my most high-value stuff in one place behind one password.
Password managers (at least the non-browser based ones) use methods provided by the OS to protect themselves from screen recording, direct memory reading and keyboard-sniffing. Most password managers can also be set up to require a keyfile and/or physical passkey to unlock their databases.
A keyfile stores data necessary for decryption separate from the password database and means someone couldn’t get into your passwords even if your database was stolen and they knew the master password (assuming you stored your keyfile separate from the database - the file and its location should be treated like a password itself). A keyfile also lets you keep your database on cloud storage while manually transferring the key to trusted devices, allowing cloud syncing of your passwords without fear of leaks - without the keyfile it’s all just random data.
A physical passkey makes it virtually impossible to breach the database unless someone steals the USB device, since it uses a challenge-response model and the data needed to spoof it should never leave the device.
-
Just got done investigating a spambot we had earlier, and it looks like they used a lot of compromised accounts on other instances to give their post an initial upvote boost. If you don’t already, please remember to use a good strong password. Keeping your account secure helps reduce spam across the whole of lemmy, and keeps your account from getting banned for things you didn’t actually do.
I recommend Diceware! I use it in my professional capacity as an IT/Security person, and also you get to use your mathrocks!
EDIT: Oh, also, all that numbers and symbols shit is no longer considered good practice. Just make it a really long collection of random words, at least 12, ideally 16+ characters. And make sure the words are actually random; your 3 favorite sports teams isn’t good enough, which is why I recommend diceware.
Over the years, nobody has ever guessed my passwords, but four sites I was subscribed to were compromised and my email+password got leaked anyway.
The strongest chain and the weakest link…
-
I’m leery of putting all my most high-value stuff in one place behind one password.
Password managers (at least the non-browser based ones) use methods provided by the OS to protect themselves from screen recording, direct memory reading and keyboard-sniffing. Most password managers can also be set up to require a keyfile and/or physical passkey to unlock their databases.
A keyfile stores data necessary for decryption separate from the password database and means someone couldn’t get into your passwords even if your database was stolen and they knew the master password (assuming you stored your keyfile separate from the database - the file and its location should be treated like a password itself). A keyfile also lets you keep your database on cloud storage while manually transferring the key to trusted devices, allowing cloud syncing of your passwords without fear of leaks - without the keyfile it’s all just random data.
A physical passkey makes it virtually impossible to breach the database unless someone steals the USB device, since it uses a challenge-response model and the data needed to spoof it should never leave the device.
I guess what I mean is, it’s a single point of failure. Usually an extremely strong one, granted.
-
these are called pass phrases and yes, they tend to be way more secure at least until quantum computers render all traditional cryptography meaningless.
Well good news then, because even throwing every quantum computer currently on the planet is not enough to factor 2048-bit RSA, and likely won’t be in any currently alive human’s lifetime.
-
Well good news then, because even throwing every quantum computer currently on the planet is not enough to factor 2048-bit RSA, and likely won’t be in any currently alive human’s lifetime.
Maybe with current quantum computers, but human technology tends to increase at an exponential rate so I doubt it will be long. Scientists are already trying to design post-quantum encryption for this very reason.

NIST Releases First 3 Finalized Post-Quantum Encryption Standards
NIST is encouraging computer system administrators to begin transitioning to the new standards as soon as possible.
NIST (www.nist.gov)
-
I guess what I mean is, it’s a single point of failure. Usually an extremely strong one, granted.
And your memory is not a single point of failure?
-
these are called pass phrases and yes, they tend to be way more secure at least until quantum computers render all traditional cryptography meaningless.
until quantum computers render all traditional cryptography meaningless.
I’ll cross that bridge when it actually happens.